Threat actors are exploiting a patched security vulnerability in Roundcube webmail to steal credentials through phishing emails. The attack, identified by Positive Technologies, utilizes a stored XSS vulnerability (CVE-2024-37383) that executes malicious JavaScript when a user opens a specially crafted message. This issue was addressed in versions 1.5.7 and 1.6.7 released in May 2024.
Understanding CDR: Mastering Your Email Deliverability with Confidence
Email deliverability is critical to the success of any marketing campaign. Understanding Campaign Delivery Rate (CDR) helps ensure your emails land in inboxes, not spam folders. In this guide, we’ll explain how CDR impacts email campaigns, and provide actionable steps to improve your email deliverability for greater engagement. Whether you’re an experienced marketer or just starting out, mastering CDR can significantly improve the performance of your email marketing efforts.
What is IPS (Intrusion Prevention System)?
An Intrusion Prevention System (IPS) is a crucial component of modern cybersecurity, designed to monitor and analyze network traffic for signs of malicious activities. By understanding how an IPS operates, its various types, and its automated response capabilities, organizations can significantly enhance their security posture. In this article, we delve into the mechanics of IPS, its benefits, and how it integrates into a comprehensive cybersecurity strategy to protect networks from evolving threats.
What is SIEM (Security Information and Event Management)? A Comprehensive Guide
Security Information and Event Management (SIEM) is a critical component of modern cybersecurity frameworks. It combines security information management (SIM) and security event management (SEM) to provide real-time monitoring and analysis of security alerts generated by applications and network hardware. In this comprehensive guide, we’ll explore the core functionalities of SIEM systems, their role in threat detection and response, and best practices for implementing SIEM solutions to enhance your organization’s security posture.
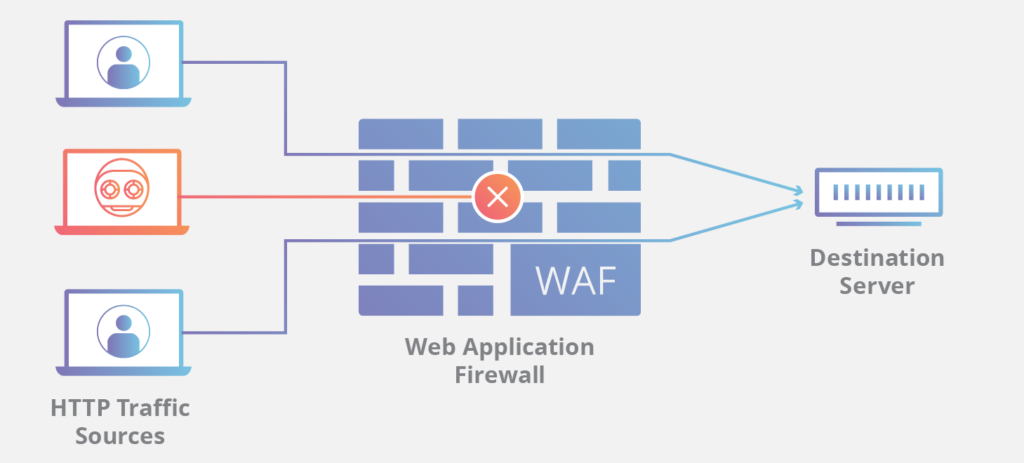
What is a WAF (Web Application Firewall)? A Comprehensive Guide
A Web Application Firewall (WAF) is a critical security tool designed to protect web applications from various online threats, including SQL injection, cross-site scripting (XSS), and Distributed Denial of Service (DDoS) attacks. In this comprehensive guide, we’ll explore how WAFs work, the different types of WAFs, and their importance in safeguarding your web-based applications. Whether you’re managing an e-commerce site, a cloud service, or email servers, understanding and implementing a WAF can significantly enhance your cybersecurity.
What Are Cookies? Understanding Their Role in Web Browsing
Cookies are small text files stored on a user’s device by websites to enhance browsing experiences. They play a crucial role in remembering login details, personalizing content, and tracking user behavior. In this guide, we’ll explore the different types of cookies, their benefits for web browsing, and the implications for user privacy. With growing concerns over data protection, understanding cookies is key to navigating compliance with regulations like GDPR and CCPA while maintaining a user-friendly web experience.
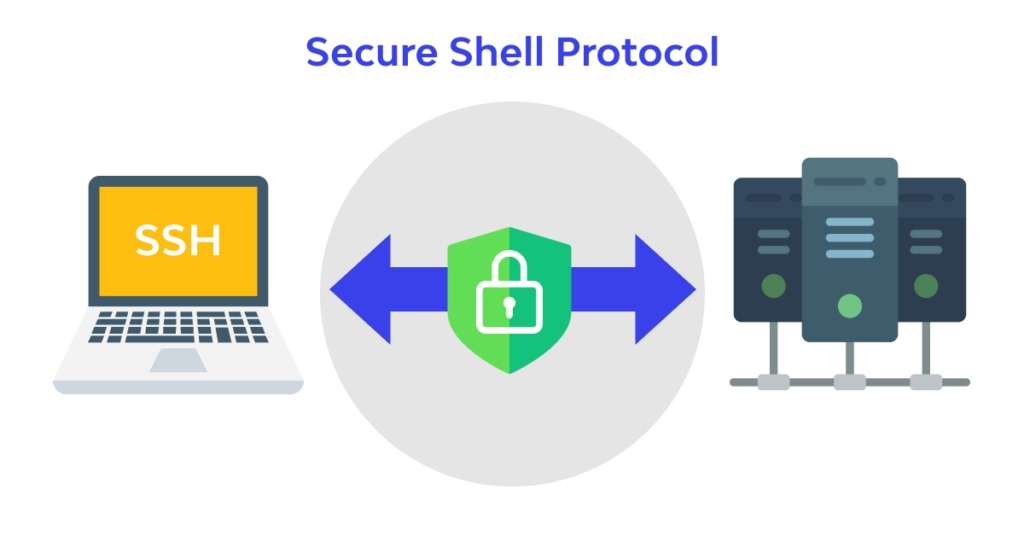
What is SSH (Secure Shell)? Understanding the Basics of Secure Remote Access
SSH (Secure Shell) is a cryptographic protocol that enables secure communication between a client and a remote server. It provides strong encryption and authentication, making it a vital tool for securely accessing and managing remote systems. This guide explains the basics of SSH, its key features such as encryption, public/private key authentication, and the various use cases for securely accessing remote servers. Whether you’re a network administrator or a developer, understanding SSH is essential for managing and securing remote connections.
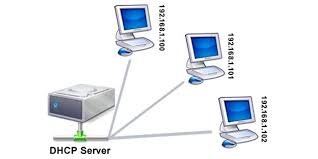
What is DHCP? Understanding Dynamic Host Configuration Protocol
DHCP (Dynamic Host Configuration Protocol) is a network management protocol used to automate the assignment of IP addresses to devices within a network. By dynamically assigning IP addresses, DHCP ensures efficient communication between devices while simplifying network administration. In this guide, we’ll explore how DHCP works, its benefits for managing network infrastructure, and how it supports smooth connectivity across devices in both small and large-scale networks. Understanding DHCP is key to optimizing network performance and reducing manual configuration efforts.
Understanding Trojans: The Silent Cyber Threat
Trojans are one of the most deceptive and dangerous types of malware, often hidden in seemingly legitimate software or email attachments. Once activated, a Trojan can compromise system security, steal sensitive data, or give attackers remote access to your device. In this article, we’ll explain how Trojans work, their different forms, and how they silently infiltrate systems. We’ll also provide practical tips for protecting yourself from these malicious threats and strengthening your overall cybersecurity defenses.
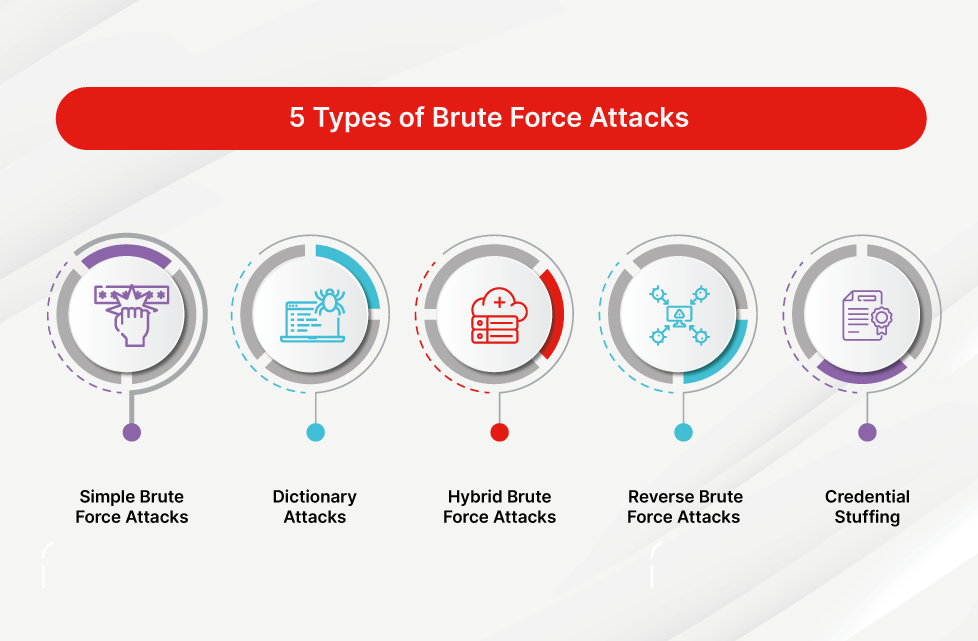
Understanding Brute Force Attacks: What They Are and How to Prevent Them
Brute force attacks are a common hacking method where attackers try to guess passwords by systematically testing multiple combinations. These attacks can target email accounts, websites, and other secure systems, potentially leading to unauthorized access and data breaches. In this guide, we’ll explain how brute force attacks work, why they are dangerous, and what steps you can take to defend against them. From implementing strong passwords to using multi-factor authentication, we’ll cover essential prevention techniques to enhance your security.