Threat actors are exploiting a patched security vulnerability in Roundcube webmail to steal credentials through phishing emails. The attack, identified by Positive Technologies, utilizes a stored XSS vulnerability (CVE-2024-37383) that executes malicious JavaScript when a user opens a specially crafted message. This issue was addressed in versions 1.5.7 and 1.6.7 released in May 2024.
Email Security
Posts focusing on protecting email communications, recognizing threats, and implementing security measures.
What is IPS (Intrusion Prevention System)?
An Intrusion Prevention System (IPS) is a crucial component of modern cybersecurity, designed to monitor and analyze network traffic for signs of malicious activities. By understanding how an IPS operates, its various types, and its automated response capabilities, organizations can significantly enhance their security posture. In this article, we delve into the mechanics of IPS, its benefits, and how it integrates into a comprehensive cybersecurity strategy to protect networks from evolving threats.
What is SIEM (Security Information and Event Management)? A Comprehensive Guide
Security Information and Event Management (SIEM) is a critical component of modern cybersecurity frameworks. It combines security information management (SIM) and security event management (SEM) to provide real-time monitoring and analysis of security alerts generated by applications and network hardware. In this comprehensive guide, we’ll explore the core functionalities of SIEM systems, their role in threat detection and response, and best practices for implementing SIEM solutions to enhance your organization’s security posture.
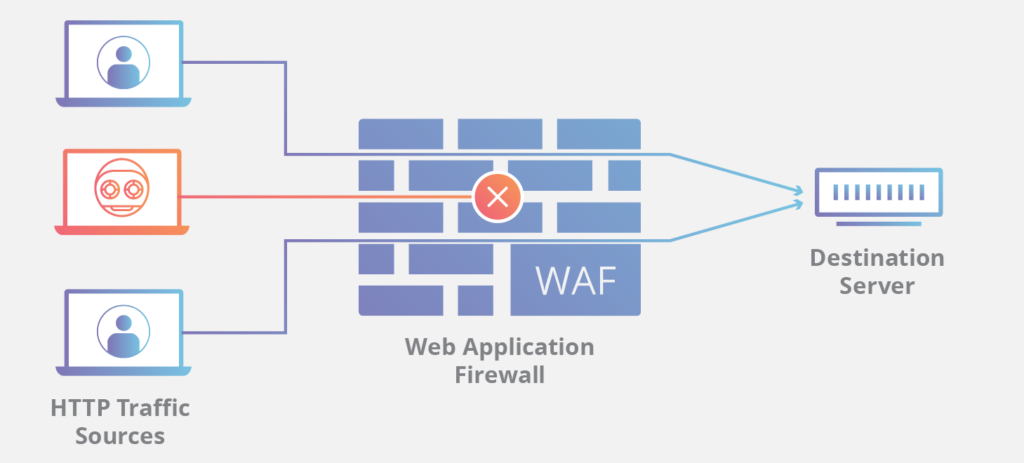
What is a WAF (Web Application Firewall)? A Comprehensive Guide
A Web Application Firewall (WAF) is a critical security tool designed to protect web applications from various online threats, including SQL injection, cross-site scripting (XSS), and Distributed Denial of Service (DDoS) attacks. In this comprehensive guide, we’ll explore how WAFs work, the different types of WAFs, and their importance in safeguarding your web-based applications. Whether you’re managing an e-commerce site, a cloud service, or email servers, understanding and implementing a WAF can significantly enhance your cybersecurity.
Understanding Trojans: The Silent Cyber Threat
Trojans are one of the most deceptive and dangerous types of malware, often hidden in seemingly legitimate software or email attachments. Once activated, a Trojan can compromise system security, steal sensitive data, or give attackers remote access to your device. In this article, we’ll explain how Trojans work, their different forms, and how they silently infiltrate systems. We’ll also provide practical tips for protecting yourself from these malicious threats and strengthening your overall cybersecurity defenses.
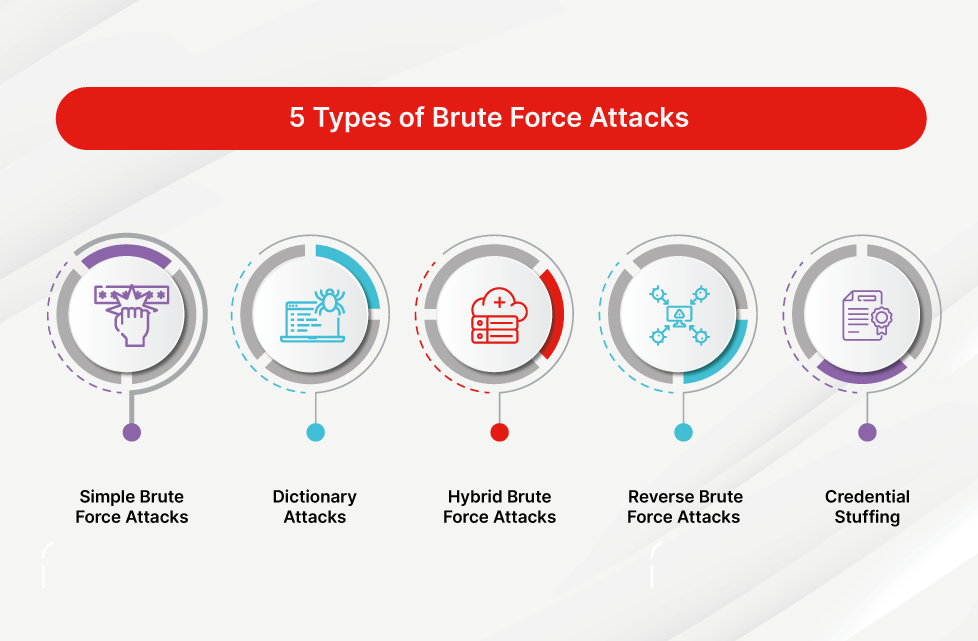
Understanding Brute Force Attacks: What They Are and How to Prevent Them
Brute force attacks are a common hacking method where attackers try to guess passwords by systematically testing multiple combinations. These attacks can target email accounts, websites, and other secure systems, potentially leading to unauthorized access and data breaches. In this guide, we’ll explain how brute force attacks work, why they are dangerous, and what steps you can take to defend against them. From implementing strong passwords to using multi-factor authentication, we’ll cover essential prevention techniques to enhance your security.
How to Ensure Network Security: Essential Strategies for Protecting Your Data
In an increasingly digital world, ensuring network security is paramount for protecting sensitive data from cyber threats. This comprehensive guide outlines essential strategies to enhance your network’s security, including implementing firewalls, using encryption, conducting regular security audits, and training employees on cybersecurity best practices. Whether you are a small business or a large organization, these strategies will help you create a robust security framework to defend against potential breaches and ensure the safety of your valuable data.
What is a Unified Mail Gateway?
A Unified Mail Gateway is an integrated solution designed to manage and secure email communications within an organization. It acts as a centralized point for routing, filtering, and analyzing emails across various platforms, providing businesses with enhanced security, compliance, and management capabilities. This article delves into the key features of Unified Mail Gateways, including spam filtering, malware protection, data loss prevention, and archiving. Learn how this technology streamlines email processes, improves communication efficiency, and safeguards sensitive information, making it essential for modern enterprises.
Email Security Against Viruses: Safeguarding Your Inbox
Email security is crucial in today’s digital landscape, where viruses and malware often infiltrate inboxes through deceptive emails. This article explores effective strategies to safeguard your inbox against email-borne threats. We discuss the importance of using reliable antivirus software, recognizing phishing attempts, and implementing strong email authentication protocols. Additionally, we provide tips on best practices for email management and how to educate your team about safe email habits. By following these guidelines, you can significantly reduce the risk of virus infections and protect sensitive information.
What to Do If Your Email Account Is Hacked.
In today’s digital age, email accounts serve as gateways to many aspects of our online lives. From personal communication to financial transactions, losing control over your email can have serious consequences. If you suspect that your email account has been hacked, it’s crucial to act quickly and methodically. In this article, we’ll explore the steps […]